Enhancing Remote Work Security with Zscaler: Best Practices and Insights
Discover best practices and insights for enhancing remote work security with Zscaler. From securing remote access to protecting sensitive data, learn how Zscaler’s cloud security platform can help organizations mitigate cybersecurity risks and safeguard their remote workforce.
Introduction:
In an increasingly remote work environment, ensuring the security of remote access and data transmission has become paramount for organizations worldwide. Zscaler, a leader in cloud security solutions, offers a comprehensive platform designed to enhance remote work security and protect against evolving cyber threats. In this article, we explore the best practices and insights for leveraging Zscaler to secure remote work environments effectively.
Introduction to Zscaler
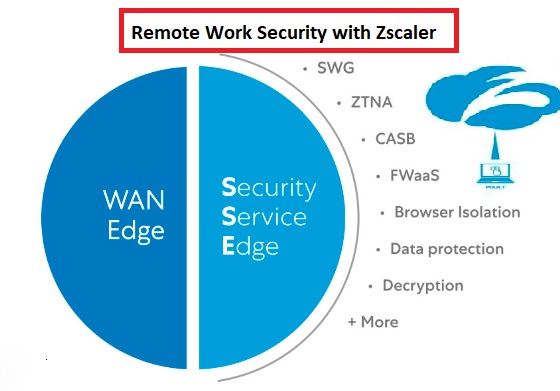
Zscaler offers a cloud-native security platform that provides comprehensive protection against cyber threats, wherever users connect to the internet. Overview of Zscaler’s Cloud Security Platform: Zscaler’s platform leverages a global cloud infrastructure to deliver secure access to applications and services, without the need for traditional VPNs or on-premises security appliances. By routing traffic through its cloud, Zscaler ensures consistent security enforcement and protection for remote workers, regardless of their location or device.
Securing Remote Access
Zscaler helps organizations secure remote access by implementing Zero Trust principles and multi-factor authentication (MFA). Zero Trust Network Access (ZTNA): Zscaler’s ZTNA solution ensures that only authorized users and devices can access corporate applications and resources, regardless of their location. By verifying user identity and device posture before granting access, Zscaler minimizes the risk of unauthorized access and data breaches. Multi-Factor Authentication (MFA): Zscaler integrates MFA into its authentication process, requiring users to provide multiple forms of verification before accessing sensitive resources. This additional layer of security helps prevent unauthorized access, even in the event of compromised credentials.
Protecting Sensitive Data
Zscaler offers robust data protection capabilities, including data loss prevention (DLP) and encryption, to safeguard sensitive information from unauthorized access and exfiltration. Data Loss Prevention (DLP): Zscaler’s DLP solution monitors and controls the flow of data across the network, identifying and preventing the transmission of sensitive information outside of authorized channels. By enforcing policies based on content, context, and user behavior, Zscaler helps organizations prevent data breaches and comply with regulatory requirements. Encryption and Secure Tunneling: Zscaler encrypts all traffic between users and applications, ensuring that data remains secure and confidential during transmission. By establishing secure tunnels and encrypting data end-to-end, Zscaler protects sensitive information from interception and eavesdropping.
Monitoring and Threat Detection
Zscaler provides real-time visibility and control over network traffic, enabling organizations to detect and respond to cyber threats quickly. Real-Time Visibility and Control: Zscaler’s cloud security platform offers real-time visibility into network traffic, allowing organizations to monitor user activity, identify potential threats, and enforce security policies dynamically. By analyzing traffic patterns and behavior, Zscaler helps organizations detect and mitigate security incidents before they escalate. Advanced Threat Protection (ATP): Zscaler’s ATP capabilities leverage machine learning and artificial intelligence to identify and block advanced threats, such as malware, ransomware, and zero-day exploits. By continuously analyzing traffic and threat intelligence feeds, Zscaler helps organizations stay ahead of emerging threats and protect their remote workforce effectively.
Compliance and Governance
Zscaler enables organizations to achieve regulatory compliance and enforce security policies consistently across their remote workforce. Regulatory Compliance: Zscaler helps organizations comply with industry regulations and data protection standards by providing built-in controls and reporting capabilities. Whether adhering to GDPR, HIPAA, or other regulatory requirements, Zscaler ensures that organizations maintain compliance while enabling remote work. Policy Enforcement and Reporting: Zscaler’s platform allows organizations to define and enforce granular security policies based on user roles, locations, and device types. With centralized policy management and reporting, organizations can ensure consistent security enforcement and demonstrate compliance to auditors and regulators.
FAQs
Q: Can Zscaler be deployed in hybrid or multi-cloud environments?
A: Yes, Zscaler’s cloud-native architecture supports deployment in hybrid or multi-cloud environments, providing consistent security and policy enforcement across all network locations.
Q: How does Zscaler ensure performance and scalability for remote users?
A: Zscaler’s global cloud infrastructure ensures high performance and scalability for remote users, with data centers strategically located around the world to minimize latency and optimize network performance.
Q: Does Zscaler offer support for mobile devices and BYOD initiatives?
A: Yes, Zscaler supports mobile devices and bring-your-own-device (BYOD) initiatives, allowing organizations to extend security controls to all devices accessing corporate resources.
Q: Can Zscaler integrate with existing security infrastructure and SIEM solutions?
A: Yes, Zscaler offers integrations with a wide range of security infrastructure and SIEM solutions, enabling organizations to streamline incident detection and response processes.
Q: How does Zscaler ensure data privacy and compliance with global regulations?
A: Zscaler adheres to strict data privacy standards and compliance regulations, including GDPR, HIPAA, and SOC 2, to ensure that customer data remains secure and compliant with applicable laws and regulations.
Q: What level of customer support does Zscaler provide?
A: Zscaler offers comprehensive customer support services, including 24/7 technical support, dedicated customer success managers, and online resources such as documentation, tutorials, and training programs.
Conclusion
By leveraging Zscaler’s cloud security platform, organizations can enhance remote work security and mitigate cybersecurity risks effectively. From securing remote access to protecting sensitive data, monitoring for threats, and ensuring compliance with regulatory requirements, Zscaler offers a comprehensive suite of solutions to safeguard the remote workforce and enable secure, productive remote work environments.